AWS networking security enhance
Vpc network division
According to the requirements of the product and the customer, the two services of the two types of subnets are isolated. For example, DBsubnet01 and DBsubnet02 are both internal private subnets and belong to different product segments.
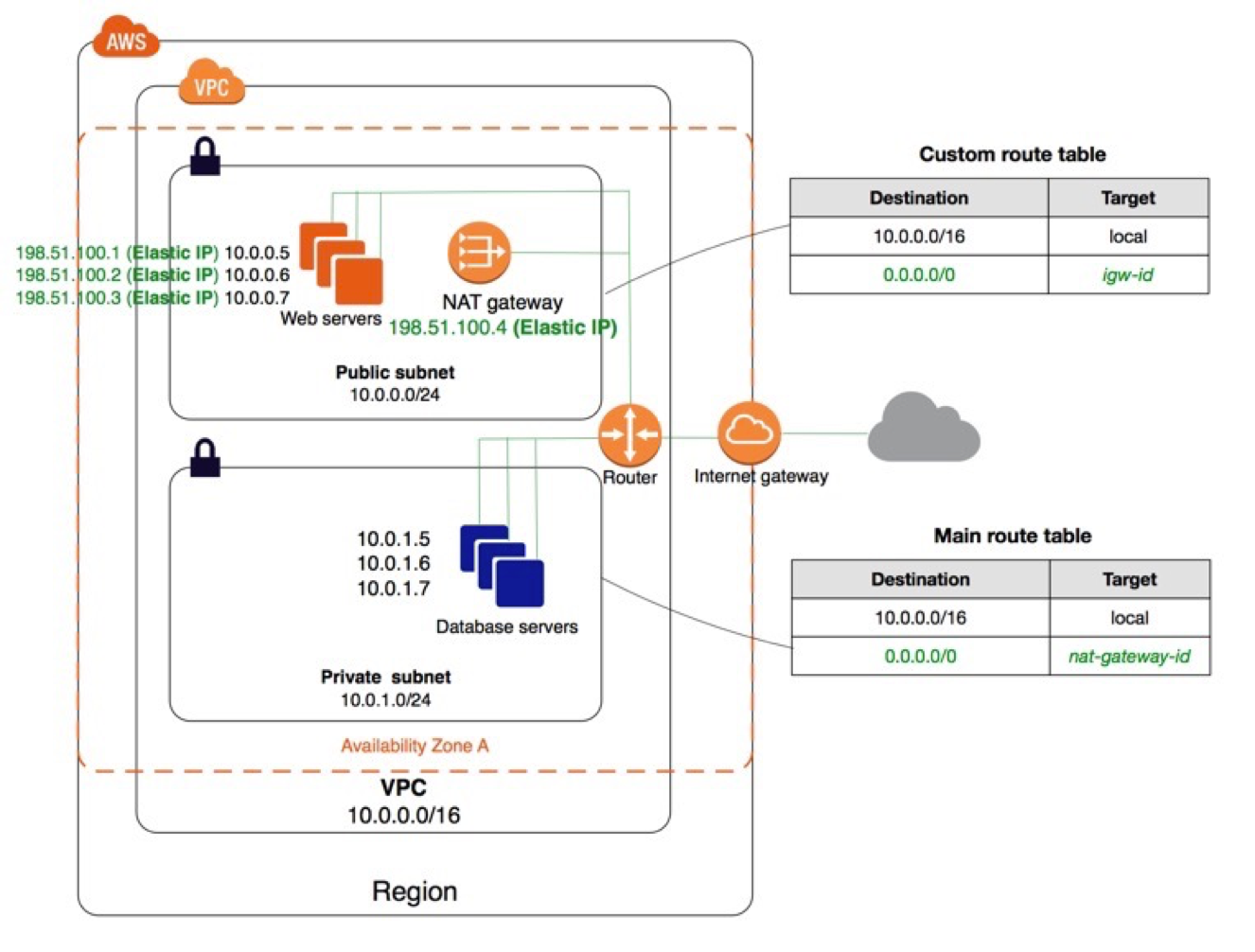
- The two major subnet types are the intranet and the extranet.
- The internal network goes to the NAT Gateway, and the external network goes to the Internet Gateway.
- Like: RDS, Redis, background services, etc. all put into the internal private subnet
- Set up a Bastion in the external subnet for proxy access to related web services deployed on the internal subnet, such as: Jenkins, SonarQube, etc.
Security Settings
We can focus on AWS’s three security door settings
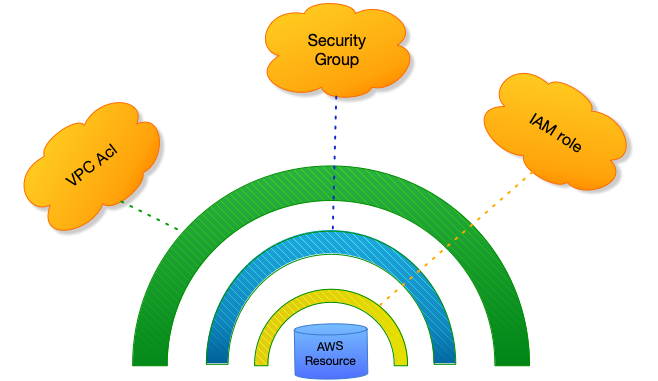
- Turn on acl and associate to all subnets
- All aws resources in use should have security groups set with minimal openness
- All Service Services that are published to aws should have the least operational rights.
Local access VPC debugging development
When debugging a program locally and connecting to an AWS VPC, we can connect in second ways.
Use Bastion machine
The local needs to be linked with the service port on aws, it can be accessed through a Bastion machine.
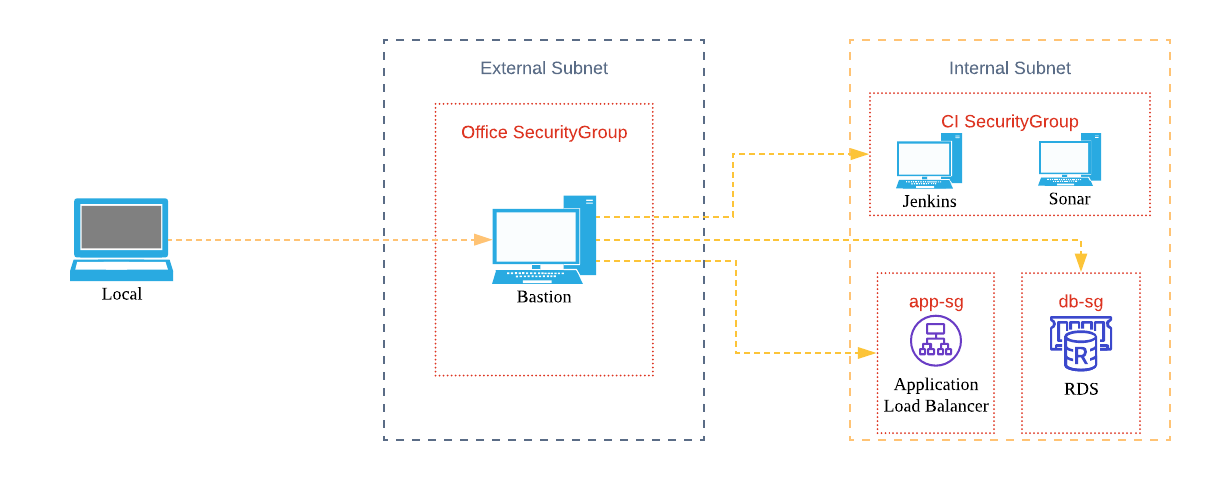
- The Bastion machine should be associated with an EIP, otherwise the public ip will be lost after the machine restarts.
- Only limited ip (office) access is allowed, and security group rules are strictly set.
- Bastion’s ssh keys should be separate and timed to rotate
- Locally, you can establish a connection from the ssh tunnel to Bastion, and then the browser can use this tunnel to connect to related tools and services through the socket proxy.
1 ssh -D 1234 -i ~/.ssh/bastion.pem [email protected] -N -f
Local browsers can access resources to aws via port 1234
- For application debugging, we can install Nginx as a forwarding rule on Bastion.
1 server {
2 server_name agent-office.exmaple.com;
3 if ($uri ~* "^/internal-app.com/") {
4 set $schemex https;
5 set $domainx internal-app.com;
6 rewrite ^/[^/]+/(?<path>.*) /$path last;
7 }
8
9 location / {
10 add_header 'Access-Control-Allow-Origin' '*' always;
11 add_header 'Access-Control-Allow-Methods' 'HEAD, PUT, DELETE, PATCH, GET, POST, OPTIONS' always;
12 proxy_pass $schemex://$domainx;
13 proxy_set_header Origin $domainx;
14 proxy_redirect off;
15 proxy_set_header X-Real-IP $remote_addr;
16 proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
17 }
18 }
- Try not to open too many endpoints to Bastion to access resources in vpc, which will bring security risks
Use Site-to-Site vpn
Site-to-Site is to establish a vpn connection between the local network and AWS vpc through the ssh tunnel.
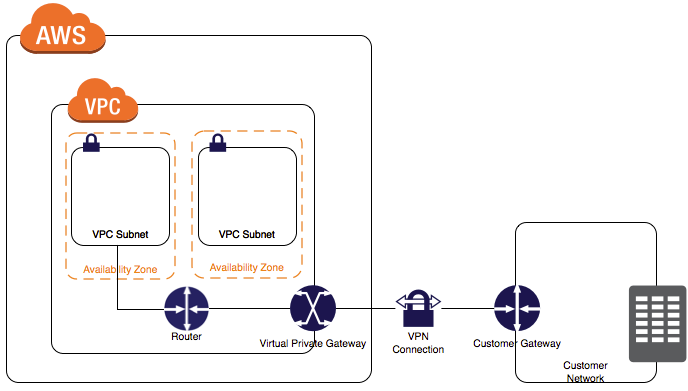
- Create gateways and vpn connections in AWS, you need to prepare in advance, the office’s external network ip and intranet ip
- In the subnet in the vpc, add the office intranet route to the relevant gateway
- Select the local router type to download the vpn configuration parameters in aws
- This way is to open aws and the office at the network level, which is most conducive to development and debugging but also brings greater security risks.